[caption id="attachment_17556" align="alignleft" width="150"] Source: Unsplash[/caption]
Source: Unsplash[/caption]
Security breaches, cyber-attacks and data leaks have certainly been a theme of 2017.
Coming off an election cycle, January was filled with debate over political hackers and disruption of the election. As if setting the tone for the months to come, the news has since been buzzing with the words “cybersecurity,” “hackers” and “data breaches.” Listed below are five of the biggest cybersecurity topics of 2017, how they were dealt with and what you can do to protect yourself in cyberspace:
OneLogin
One of the first big security breaches of 2017 was suffered by the company OneLogin. OneLogin is a password management system that allows corporate users to store passwords and other sensitive data in one place. It then uses a single password to access all the information. Obviously, this system depends on the highest level of security and makes a very tempting target for hackers.
On May 31, it was announced that the United States data center for OneLogin had been breached. Both encrypted and unencrypted customer data was stolen. The major concern with this incident was the potential exposure of millions of customers and, of course, all the online services encompassed with them.
When the breach was first discovered, the full extent and the number of people affected were unclear. An outside security specialist was hired to fully investigate and help prevent further exploits. After the incident, OneLogin recommended that users change all passwords and take other steps if using specific features.
Equifax
On September 7, it was released that Equifax, one of the three largest credit agencies in the U.S., suffered one of the greatest security breaches of all time. Originally estimated to have affected at least 143 million consumers, stolen data included sensitive information like driver’s license numbers and Social Security numbers.
Exploiting a weak point in website’s software, hackers gained access to the Equifax system from mid-May to July. During this period, they collected credit card numbers, birth dates, addresses and more. According to Equifax, the security breach affected people in the U.S. as well as Canada and the U.K.
[caption id="attachment_17558" align="aligncenter" width="480"] Source: YouTube[/caption]
Source: YouTube[/caption]
Equifax discovered the breach on July 29 and responded by seeking an outside forensics firm and setting up a link for consumers to see if their information was exposed. Today, anyone with a U.S. Social Security number can go to the Equifax Cybersecurity Website and see if their personal information was impacted during the breach.
In a further attempt to make reparations, Equifax waived fees on credit freezes and offered consumers a free year of credit monitoring, regardless of whether their personal information was exposed.
While the company did do a few things right, Equifax’s response left much room for criticism. First off, the irony of a breach happening at a firm whose core business includes protecting personal information and selling credit monitoring services to customers is hard to miss.
Secondly, he breach was discovered on July 29 and it was not until September 7 that it was released to the public. In these scenarios, six weeks is a long time. While there were likely valid reasons for Equifax waiting to go public, the delay exposed customers to further harm and additional risks. Further scrutiny was involved in the selling of shares sold by Equifax executives in the time frame after the breach happened and before the news was released.
Another mistake Equifax made in their initial response was adding to the challenges of the breach. More specifically, people have criticized how they set up their free credit monitoring services. It appeared that the sign-up for the credit monitoring services included a waiver on participation in any class action suit, which was met with a lot of questioning and scrutiny.
One major takeaway from the Equifax breach is the importance of credit monitoring and other identity theft services. My Fast PC offers its own Identity Protection and Fraud Recovery Benefits through the My Fast PC Membership Plan. These plans include identity protection services offered via EZShield, a long-standing, reputable identity protection firm and partner of My Fast PC.
In response to the Equifax data breach, EZShield has specific resources for those with compromised data. To learn more about EZShield, credit monitoring and other identity theft services, click the following link: “ Identity Theft Protection Monitoring and Recovery Services.
CCleaner
In September of this year, CCleaner reported an incident of malware that affected all software downloaded from their website between August 15 and September 7. Within a little less than a month, 2.3 million users had unknowingly downloaded a version of CCleaner software that was manipulated by hackers to be malicious.
What made this attack especially complex was that the hackers installed a second malware application on the originally infected computers. The second malware application targeted specific websites, like Sony, Microsoft and Cisco.
It soon became apparent that the attack was a focused effort to collect intellectual property within the tech industry. The compromised version of CCleaner ran for about four weeks until it was removed, and within that time it affected many companies’ machines. Some have been outlined by Cisco in a list of targeted technology companies, but it is likely that this list does not include all that were affected.
When the incident occurred, anyone using the CCleaner application was advised to check their software’s version and then delete it immediately if it was one of the two CCleaner versions affected. Uninfected versions could be downloaded on CCleaner’s main website. For a more thorough explanation of the CCleaner Hack and what users were instructed to do, see the My Fast PC article “ CCleaner Hack- 5 Must-Knows for Windows Users.”
[caption id="attachment_17560" align="aligncenter" width="960"]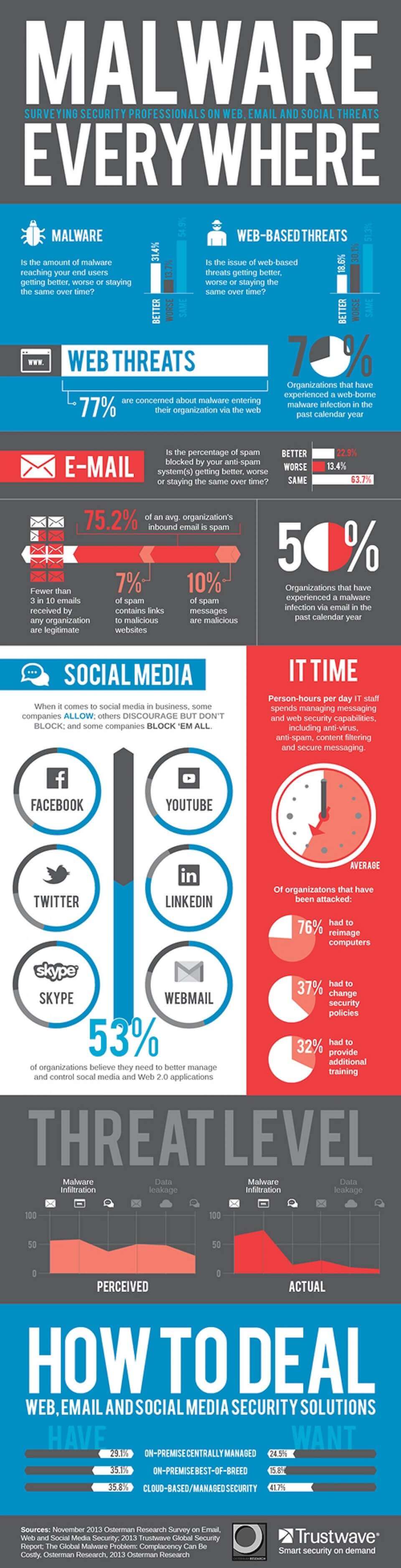 Source: Visually[/caption]
Source: Visually[/caption]
On a more general note, there are ways to avoid infection by malware. Getting a good antivirus program and updating it regularly is the first defense mechanism. A second way to avoid malware is to only open trustworthy email attachments or download software from reputable websites. For more information, see these articles on malware prevention and antivirus solutions.
KRACK
Another 2017 topic in cybersecurity was the discovery of a serious weaknesses in WPA2, a security protocol for modern protected Wi-Fi networks and the key reinstallation attacks ( KRACKs) that can be used to exploit these weaknesses.
[caption id="attachment_17559" align="aligncenter" width="960"]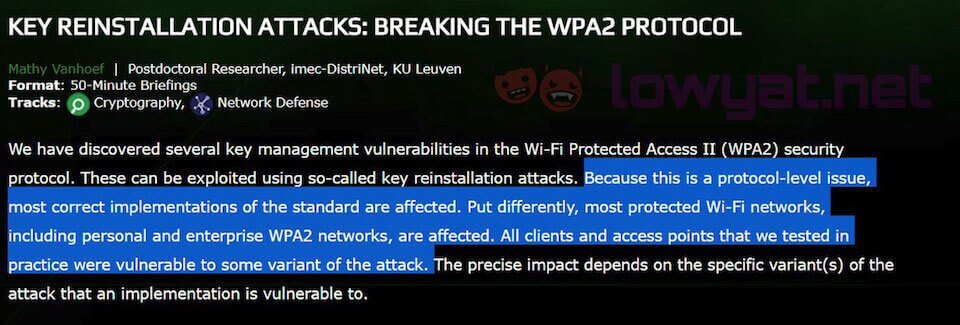 Source: Lowyat.NET[/caption]
Source: Lowyat.NET[/caption]
On October 16, researchers revealed the details of this exploit, which involved taking advantage of vulnerabilities in Wi-Fi security to tap into traffic between computers and wireless access points. Using this novel technique, attackers were able to read information that was previously assumed safe.
Working against all modern protected Wi-Fi networks, these attacks were used to steal sensitive information, like credit card numbers, passwords, emails and more. Furthermore, depending on the network configuration, hackers could manipulate data and inject ransomware or other malware into websites.
Any device that supports Wi-Fi was likely affected in this event. To prevent attacks, users were instructed to update affected products as soon as updates became available. During initial research, it was discovered that certain devices were susceptible to variants of the attack. So, Apple and other companies quickly made fixes in response to these attacks.
Another way to protect yourself moving forward is with a virtual private network (VPN) or firewall. To learn more, read “ How to Protect Yourself From the KRACK Attack.” Additional information on ransomware can be found in here.
Uber
One company that had extremely poor handling of a hacking incident this year was Uber. The Uber hacking incident happened in 2016, but did not reach the public’s ear until this year. In late November, Uber disclosed that hackers had stolen 57 million driver and rider accounts. Their company kept the data breach secret for more than a year after paying a $100,000 ransom to hackers.
[caption id="attachment_17557" align="aligncenter" width="686"] Source: ICE ICT[/caption]
Source: ICE ICT[/caption]
The stolen information included phone numbers, email addresses and names taken by two hackers. After stealing the data from a third-party server, hackers approached Uber and demanded $100,000 to delete their copy of the data. Uber tracked down the hackers and pushed them to sign nondisclosure agreements and took further measures to conceal the damage.
In comparison to other security breaches, such as Equifax, the extent and sensitivity of the breach was relatively small. What brought the incident into light, however, was how poorly Uber handled it and the lengths they went to in an attempt to cover up the evidence. An open investigation is currently underway.
General Practices and ‘To-Dos’ to Protect Oneself
While the current climate of cybersecurity can be a bit daunting, there are many things you can do to protect yourself.
Being aware of email scams and online fraud is a very important place to start. Always be careful when visiting unfamiliar websites and question suspicious email attachments. If ever in doubt, reach out to My Fast PC tech support so a professional can help you avoid potential risks.
For issues with malware, install antivirus software that’s designed for detection and prevention. These programs are often able to remove malicious or intrusive computer programs that are present on your computer while also detecting and dealing with new threats as they emerge.
You’ll also want to check your credit report and consider placing a credit freeze on existing files. Moving forward, pay close attention to your bank accounts. If any incorrect items come up, dispute them right away.
In reality, no one is safe from cybersecurity threats. 2017 was filled with inordinate amounts of security breaches and digital theft, and you can only assume there is more to come. Hopefully, as technology advances, industry leaders can learn from past breaches and provide better protection. For now, though, it’s up to consumers to take action and protect themselves.
Featured Image: Unsplash