One can never be too safe on the web. From avoiding suspicious links to ensuring your computer is free of malware, keeping yourself safe online can feel like a full-time job. Fortunately, there are tools that can help you gear up and protect yourself from unseen threats. One of the most useful tools is a browser extension (sometimes called an “add-on”).
If you feel that you are vulnerable and not savvy enough to keep yourself protected while surfing the internet then consider a membership with HelpCloud Tech Support. There’s great value in having go-to experts available 24/7. Additionally, the membership includes the best in antivirus and firewall services: Webroot SecureAnywhere.
Here is a short guide that will help you take advantage of browser extensions in an informed and safe way:
What Are Extensions?
Browser extensions give your web browser more features. Some help you modify web pages; others provide you with toolbar options and a select few help increase your online security. Simply put, extensions are useful tools that can make your life easier.
Ironically, not all extensions-even security-based offerings-are secure. Malicious extensions do exist, and if you download them, they can cause a lot of harm. You should be very careful when you download browser extensions. Corrupt offerings can snoop on your browsing history and gain important information from your online activities, such as your bank account details. Luckily, there are a few tried-and-true extensions from well-known developers that have minimal risks. These offerings are presented in the “Five-Star Extensions” section below.
Depending on the browser you use, you will have different extensions at your disposal. People that use a Firefox browser have access to advanced extensions that are often more technical. Chrome users can download an extension for pretty much everything they can think of. There are nearly unlimited options, and many of them are known for their high-levels of security.
If you use Internet Explorer, your extensions options are not as plentiful. There are a few options on the market, but they’re not nearly as comprehensive as the choices for the aforementioned browsers. Similarly, Safari and Opera have small extension ecosystems that are fairly limited in scope.
Browsing Tracking
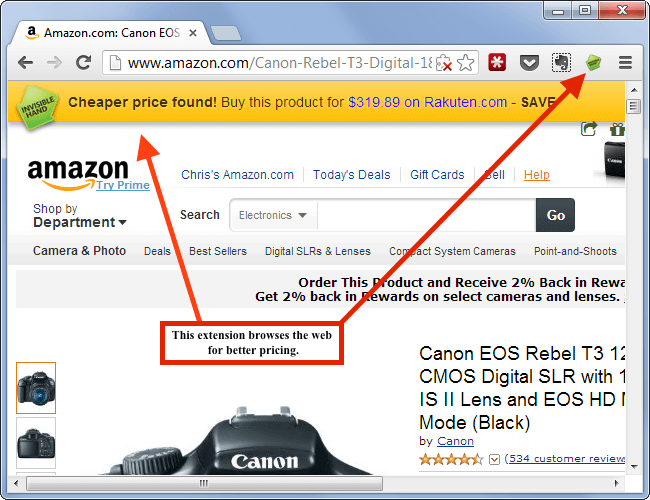
Browsing extensions are more dangerous than most people realize. Many of them have access to everything you do online. This information can be used for various activities-one of which is identity fraud. Another common downside of extensions is unwanted advertising.
Extensions are so dangerous because they’re tied to your web browser. Many of them even have the ability to read or change the information on the web pages you visit. Since an extension has access to all of your web traffic, it can do practically anything. It may be a keylogger, which can capture your passwords and credit card details. Extensions even have the power to redirect your search traffic elsewhere.
Not all extensions do corrupt things, but nearly every single one has the power to do so. This is why users should be very, very wary of which ones they use. Some online aficionados recommend that people use Google Chrome and its extensions because Google has additional security measures in place for their offerings. That being said, even Google has trouble with its extensions from time to time.
Two months ago, one of Chrome’s most popular extensions was hacked. An attacker changed the extension so that it would load more advertisements onto users’ web pages. Over a million people ended up with the infected extension on their computers. Luckily for them, the attack was fairly harmless. A worse version could have been distributed that was designed to steal private information.
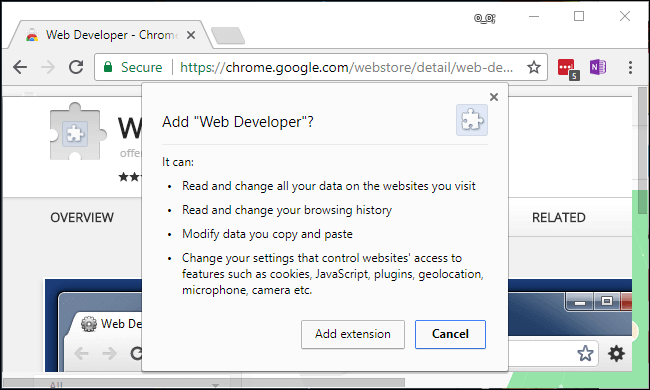
It’s not uncommon for trusted extensions, like Chrome’s Web Developer, to have problems. This is because modern web browsers often update automatically. New versions run with the same permissions as in the past, which is really harmful when the new extension is compromised. Furthermore, some extension owners willingly sell their software to companies that then modify them for advertisements and tracking. Without knowing it, all existing users start to use the new advertising- or tracking-based extension when their browser updates.
Five-Star Extensions
HTTPS Everywhere is an extension for Firefox, Chrome and Opera that encrypts your communications with websites. On certain sites, or specific parts of them, the software protects against others eavesdropping on your online activity and tampering with your information.
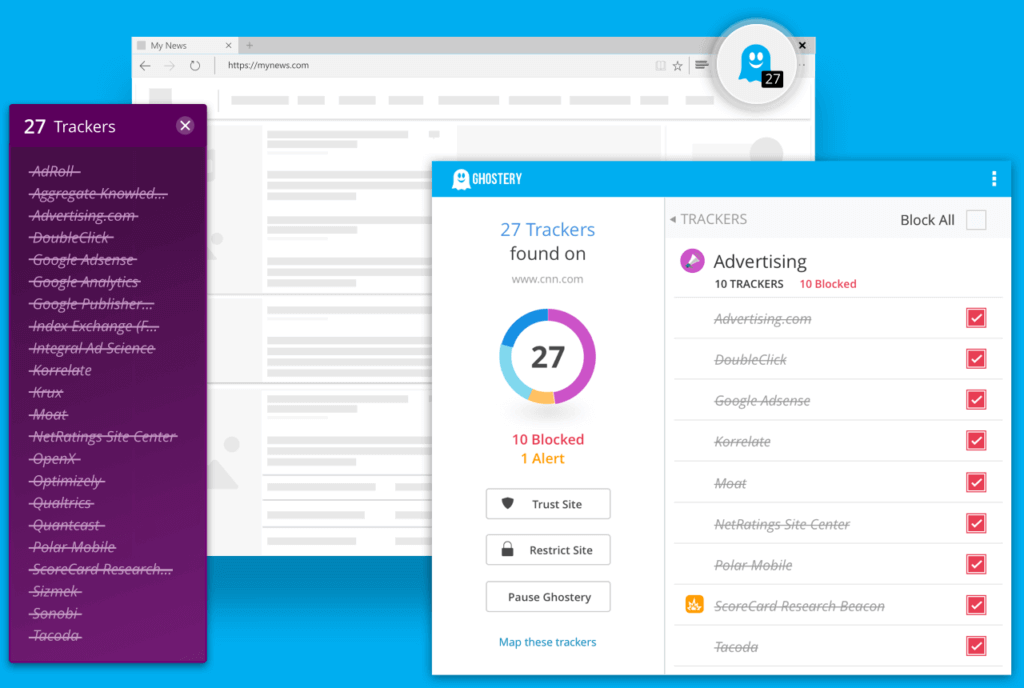
Another option is Ghostery, an extension that detects and blocks tracking technologies. Their extension is only available on Chrome. However, they do have mobile-based offerings for Android and iOS.
LastPass is a Chrome and Firefox extension that helps manage your passwords. Their goal is to make your passwords easier to secure and remember. This extension can remember all of your login information for you, and it can also store sensitive info-like your credit card numbers.
Limiting Your Use
The best way to use extension technology safely is to limit the amount you use. From a security standpoint, the more you have, the more risk you’ll experience. Remember, extensions are commonly corrupted, so the more you have, the more likely you’ll be infected.
From an operating standpoint, extensions can make your computer run differently. The more extensions you use, the less memory you’ll have. Your system may start to slow down when you use two or more extensions. The benefits they offer may not be worth the sluggish speeds they create.
To determine the impact a browser extension has on your system, you can run various tests. Unfortunately, there aren’t a lot of beginner-friendly ways to view your browser extensions and understand their memory usages. So, if you need help, reach out to the online computer support and repair company My Fast PC.
Customizing Your Extensions
To use extensions safely, you’ll need to know how to configure their settings. Google has a useful guide that can help you manage all of your Chrome extensions. Firefox also has an online resource that can help you understand how to customize and monitor their extensions. Their page is called “Find and install add-ons [extensions] to add features to Firefox.” You can find information on Internet Explorer extension management here, Safari here and Opera here.
Regardless of the browser you use, you should know how to turn your extensions on and off, how to disable them and how to uninstall them. Again, this can be a bit confusing, but companies like My Fast PC can help you understand and master the process.
Tablet and Phone Add-Ons
Add-ons aren’t only for your computer. Any device you have that has a web browser should be able to use extensions, too. Interestingly enough, there’s even a way to use Chrome extensions on Android devices.
If you want to install a Chrome extension on your phone or tablet, the process is quite easy. First, you’ll sign into Chrome on your device. In the same chrome window, search for the web extension that you need. Once you’ve found it, select “Add to Desktop.” A window will appear, and you’ll select “Add to Desktop” one more time.
After this process is complete, the extension will be installed remotely. It should start running right away, unless it needs permissions. If the extension needs specific access, you’ll have to grant it by clicking “Enable extension.”
Why Do Extensions Want Your Info, Anyway?
A lot of what you see on the internet is advertising. Sometimes, advertisements help you find a product that betters your life, but other times they just stuff up your computer screen and make online searching annoying. To decrease the negative aspects of advertising, many users take advantage of ad blocking software or pop-up blocker extension.
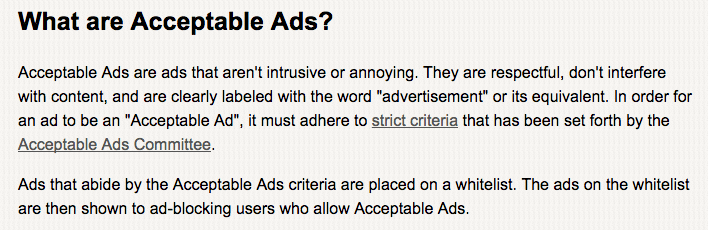
It’s hard to make money off blocking software. Some companies in the ad-blocking industry make money, and others don’t make any money at all. One group that does make a profit is “Adblock Plus.” Instead of cutting out all advertisements, it simply shows you “acceptable” advertisements. Content is deemed acceptable if it meets specific criteria, such as placement, size and distinction. Companies with “acceptable ads” pay Adblock Plus for soliciting their businesses. Other companies have revenue-generating models that are based off selling your information to advertisers.
Summarizing the Above Findings
Internet add-ons can make your online experience much more enjoyable. That being said, they can also make your computer vulnerable to malicious attacks. It’s vital to understand the risks extensions present before you decide to install them. After all, if your identity is stolen, you probably won’t feel like the extension was worth the hassle.
There is a cautious way to use add-ons and mitigate the risks they pose. Make sure to only use a few extensions, and keep up-to-date on industry news. If there is an issue with your extension, it’ll probably be made public at one time or another. If you’re aware of current news, you’ll be able to update your computer browser as soon as possible and hopefully avoid harm.
For some, extensions are more cumbersome than they are helpful. Various users will want to leave their browsers in their simpler forms to avoid extra work, risk and possible confusion. Others may find that the added functionality is well worth a little more upkeep and some risk.
At the end of the day, the decision is yours, but you don’t need to make it alone. Reach out to an online computer support company that can help you gain a better understanding of the pros and cons of extensions.
If you feel that you are vulnerable and do not feel savvy enough to keep yourself protected while surfing the internet then consider a membership with HelpCloud Tech Support. There’s great value in having go-to experts available 24/7. Additionally, the membership includes the best in antivirus and firewall services: Webroot SecureAnywhere.