Would you be comfortable leaving your house unlocked overnight if you knew for certain someone was going to try and break in? Do you want to put your safety and privacy in the hands of a complete stranger?
If you’re like many Americans, the answer to the above questions is likely a resounding no.
That being said, what if you learned that the internet is somewhat like an unlocked house? Seriously, you probably already store a lot of your valuables and private information on the web without really knowing how to protect yourself.
Before delving into learning about protecting data, one must learn why the internet is insecure and why it can never be made totally safe. One of the main reasons the internet can never be fortified is due to its limited beginnings.
The web was originally built to let massive supercomputers communicate with one another. Computers used to be so large and costly that only big governments and huge businesses / universities owned and operated them. When these supercomputers started transmitting information back and forth, a network was established.
The new network slowly expanded until it was common enough for personal computers to be created. Now, the internet has exploded. You can talk with others online, shop, bank, play games and even use the internet’s technology to age in place.
Other devices can even communicate with the network, which is why we have the Internet of Things (IoT). Countless devices, from home appliances to vehicles, can talk with each other over the internet.
Although the convenience and ease of devices talking amongst themselves has many upsides, it also comes at a price: security. A single corrupt device can transmit viruses and malware to other devices on the network. A online criminal can even steal your identity by guessing or cracking your online passwords.
Unfortunately, multiple flaws are built into the internet’s very setup.
There will never be a time when criminal activity and security threats can be removed from the network. A totally secure internet would hinder downloads, uploads and installations.
All traffic would be heavily regulated by governments, private organizations, public organizations, bots and more. A perfect internet would have an extremely limited amount of websites and possible functions.
Also, even with all of these limitations in place, it’s likely that some criminal would eventually break through all the safeguards to carry out corrupt online actions.
The internet isn’t changing anytime soon, but that doesn’t mean that you can’t participate. The system is flawed, but according to cybersecurity experts, there are ways you can protect yourself.
The Internet of Things and Smart Devices
The IoT has changed a ton about the world you live in today.
Many of the devices around you have smart sensors built into them that connect to the internet. Said devices then transmit data over the internet, which is ultimately supposed to help devices work better alone and together.
A good example of this is a smart car.
Imagine you’re taking a smart car on a long road trip, and as you’re arriving at your destination, your check engine light comes on. When the light illuminates, you know there’s probably an issue, but you don’t know what’s wrong or what local mechanics might be able to help.
The issue triggers data to be sent to your manufacturer, and a customer support representative emails you to let you know that there’s a recall on a component in your brake line.
Instead of having to find a repair shop in an unfamiliar town when you’re on vacation, you know that you can take the car to your go-to shop when you return home after your trip.
What if things didn’t go so smoothly, though?
In the aforementioned example, think about what would happen if a criminal hacked into your car. He or she could send you an alert and give you the impression that your vehicle requires a check.
Then, the criminal could send you a text letting you know your car needs to be serviced right away, and he or she could provide you with GPS directions to a nearby location.
When you arrive at the address of the supposed repair shop, a criminal may meet you and then force you to hand over the keys to your car. The thief could also have other criminals break into your house while you’re away on your trip.
It’s clear to see that the advantages and disadvantages of connected devices are both very prevalent, which is why cybersecurity experts are working tirelessly to help people protect themselves when using the IoT and smart devices in and outside of their homes.
The Past
Hypotheticals are important, but they have their limitations. Past events can provide a more accurate understanding of what can happen when the internet is corrupted.
Last year, Bluetooth, one of the most popular wireless communication technologies, had eight serious vulnerabilities. Hackers were creating corrupt devices that would automatically infect other pieces of technology when they came into Bluetooth range.
Overall, this attack affected over 5.3 billion devices. If this wasn’t bad enough, top security experts say that almost half of the impacted devices will never be patched.
Current Events
In June of 2018, Jamie Summit, a mother who had recently given birth, realized that an unauthorized individual was controlling her baby monitor.
At first, when the camera was moving without her telling it to do so, she figured Kevin, her husband, was controlling the camera from his smartphone app.
Later on, the camera moved again, but everyone who uses the app was together, and none of them were controlling the device. Much to Summit’s horror, she realized that the video was slowly moving across the room to where her bed was located.
It stopped panning in the spot where Summit commonly breastfed her newborn. The family instantly unplugged the monitor, but it was too late. She was already locked out of her account, and the damage had been done.
Looking Forward
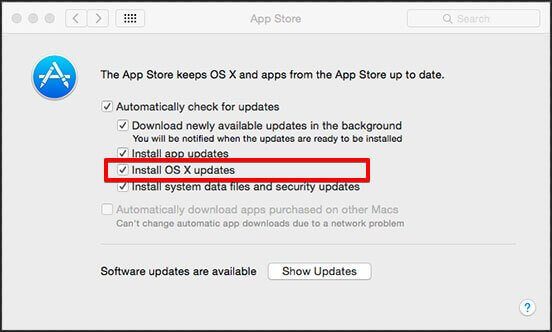
An operating system (OS) has to be updated regularly for many reasons, but especially to ensure it receives proper patches to security flaws.
With countless smart devices, how do you make sure the operating systems in your smart thermostat, light bulbs, TV and fridge are all up to date? As of now, there’s no current standard for users to update their devices when security updates are rolled out.
In the near future, you might start to see criminal activity that’s associated with security flaws in outdated devices. Even when people know there are important security updates available, they don’t always take the time to download and install them.
According to a study from Brigham Young University, “People ignore software security warnings up to 90 percent of the time.”
Tips From Cybersecurity Experts
1) Lock Your Devices
Every device you own should have a password.
Whenever you’re not actively on a device, ensure it’s locked.
According to ComputerShopper.com, “It’s always a good idea to lock your PC if strangers are nearby and you step away for a few minutes. Just press Windows key+L to lock your PC. Alternatively, you can set your screensaver (via the Screensaver tab in Display Settings under Control Panel) to require a password if it’s deactivated by checking the box in ‘Settings’ that says ‘On resume, password protect.”
2) Create Separate Networks and Profiles
You don’t want to access your bank account information on the same network as you shop for your smart fridge. If you do, someone may hack into your fridge to gain access to all of your financial information. To limit the amount of privilege any given network has, “Practice the principle of least privilege,” says Indiana University.
“Do not log into a computer with administrator rights unless you must do so to perform specific tasks. Running your computer as an administrator (or as a Power User in Windows) leaves your computer vulnerable to security risks and exploits.
Simply visiting an unfamiliar internet site with these high-privilege accounts can cause extreme damage to your computer, such as reformatting your hard drive, deleting all your files and creating a new user account with administrative access.”
3) Update Your OS
As alluded to earlier, you always want to update your operating system. California SBDC states, “To make this easier, more software programs, including Windows, Office, Flash, Java and Adobe Acrobat, now offer options to download and install updates automatically; these can generally be accessed through ‘Settings’ or ‘Preferences.'”
4) Look Into Your Router
Norton Security considers routers to be ” The front door to your smart home. “
The corporation advises customers to start protecting themselves by investing in a sound WiFi router. Once you have a solid device, you should change the username and password and replace them with unique, strong login credentials.
5) Stay Away from Public WiFi
Comodo Security Solutions advises all of its clients to “Turn off the ‘automatically connect’ option on phones to take precautions and not get connected to the public WiFi found in malls, coffee shops and airports.”
It’s easy for hackers to intercept the data you transmit on a public connection, putting your personal information and overall security at risk.
Connect With a Computer Support Company
If you want to protect your house, you lock your doors and sign up for a membership with a home security company. To protect your information online, you follow the advice above and sign up for a membership with a computer support business.
There are countless reasons to have a membership with a technical support company, especially as the IoT continues to expand.
The top computer assistance companies are constantly checking in with cybersecurity experts and learning about the past, present and future IoT, smart devices and smart home vulnerabilities, so you can stay safe with the most up-to-date information.