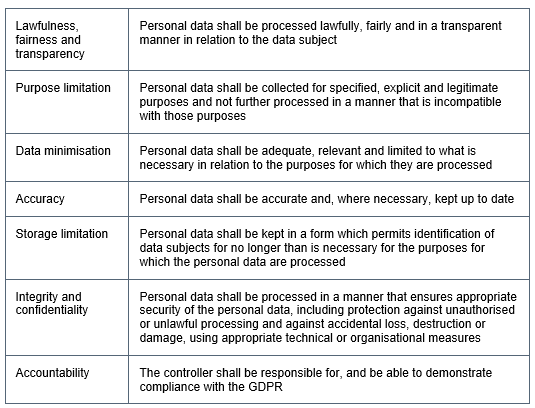
GDPR (General Data Protection Regulation) as explained in our detailed article here is, in summary, a series of protocols that creates rules for businesses that do business in Europe on how to process and maintain data collected from European residents. The new regulations in the European Union (EU) not only make businesses subject to heavy penalties and fines when not in compliance but also focus on seven key principles that aim to protect the fundamental rights of a user while online:
Since its inception in legislative proceedings and especially since its implementation there has been debate on the implications of such a broad reaching and impactful regulatory practice. Arguably, GDPR impacts companies that may be based outside of Europe but only have a minor inkling of interaction with European users. As it is now in effect we have yet to see the rollout of unforeseen implications of such a game-changer. Such an impactful legislation implemented by government also raises the question of what about governments and their collection, protection and usage of private data? Who and how will certain groups exploit the regulations, e.g. will lawyers and residents bog down court systems with unnecessary and ambiguous lawsuits in hope for easy winnings? What are the cybersecurity implications of GDPR and are they as positive as we think? We can expect that a paradigm shifting regulatory behemoth has both pros and cons.
The U.S. may see similar legislation in the future. We can learn many things as Europe moves forward with this experience. In the meantime it is important to consider how you, as a private user, can self-GDPR, i.e. protect your own personal data and privacy.
So What’s Next?
Simply put, businesses that don’t want a fine of up to a 20 million euro or 4% of their worldwide annual revenue will have to do a good job ensuring that their websites, emails, etc. are in complete GDPR compliance. This is no easy feat especially considering most major companies have to create, for some, an entirely new position called the “Data Protection Officer” ( DPO) as well as create processes that:
- Acquire explicit consent from the user
- Detect and notify all users of a data breach within 72 hours
- Provide, as requested, electronic information and complete transparency in how the company uses the user’s personal data
- Data Ensure: a process for opt-out or the right to be forgotten, i.e. by user request the deletion of any information or data no longer needed
It is a no-brainer for businesses to be in compliance. Even companies, such as HelpCloud, regardless of not having customers in Europe are working to implement GDPR compliant processes.
Internet Service Providers (ISPs) and telecom businesses in Europe are also subjected to stringent regulations under GDPR. Storage and usage of consumer information must be used with consumer consent. In the U.S. we are subjected to quite the opposite regulations when it comes to ISPs. U.S. based ISPs as of recently can collect and sell consumer data without knowledge or consent. In Europe a user can simply request from the ISP a copy of all personal data stored by the ISP but in the U.S. you have no such easily accessible transparency.
This is likely to be a headache for telecom businesses but needed as they have the most direct access to some of our most personal and private data and online behavior. This prevents ISPs in Europe to sell personal data or grant unfettered access to advertisers to unknowing consumers. An ISP is not an advertisement network after all.
But What about the Government?
At its core it is a solid and necessary piece of legislation that will dramatically help curtail the abuses and gray areas practiced by businesses when it comes to data collection, utilization, and reselling. But this legislation was purely for the private sector in order to protect the public. So what about the public institutions funded and ran by the same people that are protected under GDPR? What impact does GDPR have on a governing institution? What will the federal governments in France, Germany, Belgium, and more do because of GDPR?
The short answer: nothing.
There is nothing in the legislation that targets the practices of national governments that are members of the EU. They differentiate the collection of data by a government and businesses as following, “under EU law, the right to privacy and the right to protection of personal data are two distinct fundamental human rights.”, but the line seems to blur here as a tech company does in fact need to consider and protect the right to privacy of a user.
The European Parliament further distances itself from national authorities collecting and processing citizens private data by allocating all such activities to the nation alone, and stating, “The Court of Justice of the EU does not have jurisdiction over cases that involve surveillance conducted by national authorities in order to safeguard the internal security of the EU Members. ”, but this raises the question if the EU Parliament can regulate the abuses of personal data and user privacy conducted by private businesses should it not do so, or at least have a standard, for its members and the potential abuses of personal data conducted by governments?
Are There Cons with GDPR?
The pros of GDPR are highlighted in the principles and processes that the regulatory document requires. The pros are definite user protection and control of personal data. GDPR is, for the idealist, a champion for user rights and privacy advocates. Positivity regarding this legislation is far-reaching and unsurprisingly so. GDPR champions the rights of and consent from your everyday internet user. It also targets gray-area and undoubtedly black hat tactics that have exploited unsuspecting people browsing the internet.
One would be naive to think that such a move will have none or little negative impact. While larger companies (and many of these are the most guilty of this abuse) have had the funds available to prepare for this paradigm shift, there are many smaller companies in and outside of Europe that are, for many reasons, unable to understand the scope of these regulations and how to prepare and remain in compliance. As when any large power, especially governments vs. larger corporations, goes after its target the bystanders are caught in the crosshairs.
Let’s breakdown the potential pitfalls, negative impact, and cons of GDPR. Doing so would do us all the favor of approaching the legislation critically rather than in blind faith.
Societal Impacts
While we will soon breakdown specific potential pitfalls or cons of GDPR, it is important to begin with the conceptual or social impact of the regulations. While on some levels it informs, it also hinders the responsibility for the user to take certain steps to being critical and thoughtful in their digital actions. Will it build a false security net? How will this reliance of GDPR be exploited in the future?
While the cliché “give a man a fish and you feed him for a day; teach a man to fish and you feed him for a lifetime” is a bit too often referenced, it is nonetheless relevant and applicable with how a user behaves on the internet. As the internet is a tool it is then important that its users learn how to use the tool. Any tool that is powerful has potential for harm or potential for meaningful and good use. We are not by any means excusing those that abuse and prey for victims on the internet but rather the point is that a user on the internet must learn to protect themselves and their data as well as the data for which they are responsible, e.g. at their work, of their children or direct relatives, other close and loved ones, etc.
The foreseeable danger with overarching regulations like GDPR is that a user will become lazy and rely on governing institutions to regulate and execute punishment for those that violate said regulations.
There is, of course, at this time in history far too many that profiteer from data without consent as well as those that pass this information, without explicit consent, on to third parties who far from have the user’s best interest in mind. The regulations are necessary and GDPR is bold. We can hope and push that its refinement leads to a consensual and balanced power structure on the internet.
Practical Negative Impact
Websites Being Blocked or Blocking European Users
Legitimate websites are either blocking EU users or are being blocked in the European Union. High profile websites like The Chicago Tribune, LA Times, and Orlando Sentinel were not accessible by EU users on GDPR’s launch date. This raises the question to which lengths the EU will go to block, control, target, etc. websites that they find are not in compliance. Where is the freedom of the user when a commission decides the websites accessible if you have a EU IP address? Many power users understand the risks and implications of visiting certain websites and they take the necessary actions to protect their devices and data. Is this an impediment of internet freedoms if the GDPR evolves into a form of firewall or censorship, similar to other countries where said firewalls are considered by Westerners to be a form of censorship?
Consent or No Access to Website
Websites like Facebook, Google and their subsidiaries have created new terms and conditions to which a user has to agree (including targeting advertising) if the user desires to keep using the product. Without consenting, the user is barred from the service. This raises the question of the ethics of who holds the most power in this situation. Does a user have the right to demand access to services without payment while nitpicking the terms and conditions? Or do the controllers of the product have the power to demand full consent or no service? Targeted advertising is a large reason why we can access these services without payment. The user’s payment is being subjected to advertisers that are able to target you based on your search queries, hobbies, etc.
What is the middle ground here? Do we have the option to shut off targeted advertising, or even block advertising completely? At this point we shouldn’t be surprised if the website demands monthly payment for its services. There are certainly many that would consider and prefer this option over the exposure of their data to outside parties. Then there are those that prefer targeted advertising, especially if it ensures an otherwise free service.
Non-EU Websites Penalized without Desire to Participate in the EU
Does the GDPR overreach its jurisdiction by imposing regulations on websites that unwittingly have European citizens integrated into its data processing or technical stack?
Example: a website that sells software to households and small businesses only in the U.S. also has a YouTube channel which is available to anyone anywhere (because that’s the beauty of the internet) so long as the country does not block YouTube. A user from the EU then visits a YouTube video from this company, then the website and then enrolls in the monthly newsletter via a double opt-in, granting permission to the company to process their data. This website is in complete compliance with all the laws and regulations in the United States. Are they then beholden to laws and regulations from Europe if, by no intent of their own, a consenting EU user has found and connected with them? If they do something that violates GDPR are they subjected to fines and penalties?
This gray area may already have an answer but just because it is clear to experts what will happen in this scenario doesn’t make it clear for uncertain smaller businesses outside of the EU. This is an example of the uncertainty caused by a legislation enacted by the EU, what should only impact those whom they govern. But the reality is that the internet was enjoyed by many people because it did not have borders. The imaginary geopolitical lines were transcended by the tool and at its best the internet is humanities most unifying asset. GDPR highlights how interconnected the internet and its users are and how impactful a major legislation in Europe, or other world powers, can ripple and influence the whole world. Do they have that right to unilaterally govern the internet?
Potential Pitfalls from the Right to be Forgotten
For your everyday user this is a great and positive consequence of GDPR. The right to erasure allows a user to control the content published containing their personal data online. The question here is what will those in power do and to what extent will they go to control the narrative of who they are and what they do?
The European Commission has published an answer to this question and in it they cite that a politician does not have the right to ask a news source to delete a story highlighting their corruption due to fact the news source is exercising their right to freedom of expression. But only an idealist living in the clouds would think there will be no lawsuits pursued by those with the funds to prove that they have the right to erasure while, in reality, attempting to censor and control the public’s narrative when discussing said person’s politics, social stances, company practices, potentially unethical practices, etc. Is this an avenue to potentially erode the rights in a democracy to freedom of expression and information as well as the transparency of those in power?
GDPR May Weaken Security
What impact will the changes needed to be in compliance with GDPR have on security expert tools and how they track and detect cybercriminals? Two of those tools are ICAAN ( Internet Corporation for Assigned Names and Numbers ) and WHOIS. In this article you can further understand the necessity for the WHOIS and similar tools for cybersecurity experts. In short, ICAAN’s mildest of proposals to bring domain registrars in compliance with GDPR would hamper the current tactic of tracking down illegitimate activities online:
Responses by cybersecurity experts to ICAAN proposals and GDPR are as follows:
Brian Krebs of KrebsOnSecurity writes, “…many security experts are worried that the changes being ushered in by the rush to adhere to the law may make it more difficult to track down cybercriminals and less likely that organizations will be willing to share data about new online threats.” Source
From Brian Krebs:
For my part, I can say without hesitation that few resources are as critical to what I do here at KrebsOnSecurity than the data available in the public WHOIS records. WHOIS records are incredibly useful signposts for tracking cybercrime, and they frequently allow KrebsOnSecurity to break important stories about the connections between and identities behind various cybercriminal operations and the individuals/networks actively supporting or enabling those activities. I also very often rely on WHOIS records to locate contact information for potential sources or cybercrime victims who may not yet be aware of their victimization.
…
Many privacy activists involved in to the WHOIS debate have argued that other data related to domain and Internet address registrations — such as name servers, Internet (IP) addresses and registration dates — should also be considered private information. My chief concern if this belief becomes more widely held is that security companies might stop sharing such information for fear of violating the GDPR, thus hampering the important work of anti-abuse and security professionals.
This is hardly a theoretical concern. Last month I heard from a security firm based in the European Union regarding a new Internet of Things (IoT) botnet they’d discovered that was unusually complex and advanced. Their outreach piqued my curiosity because I had already been working with a researcher here in the United States who was investigating a similar-sounding IoT botnet, and I wanted to know if my source and the security company were looking at the same thing.
But when I asked the security firm to share a list of Internet addresses related to their discovery, they told me they could not do so because IP addresses could be considered private data — even after I assured them I did not intend to publish the data.
…
Certainly as the Internet matures and big companies develop ever more intrusive ways to hoover up data on consumers, we also need to rein in the most egregious practices while giving Internet users more robust tools to protect and preserve their privacy. In the context of Internet security and the privacy principles envisioned in the GDPR, however, I’m worried that cybercriminals may end up being the biggest beneficiaries of this new law.
At HelpCloud we rely on IP lookup capabilities to determine whether irregular activity is part of a bot network (we have also discovered smart devices, e.g. an Apple Watch, most likely part of an IoT bot network) fraudulently clicking our advertisements. Having these insights makes it easy to determine whether we will block the IP and protect our site and its users.
As Brian Krebs also has highlighted, internet users need more robust tools to protect and preserve their privacy. I envision a future world where every internet user is a critical user, where they take security in their own hands, know the implications of sharing their information, what they are clicking, where they have landed, and how to correct security breaches on a personal level. An educated, critical, and aware population of internet users will be the best fight to quelling the impact and reach of cybercriminals and businesses that overreach and violate data and personal privacy. This is combination with similar legislation like GDPR will lead to an internet worth protecting and an internet for all. What does this look like from a practical standpoint?
Self-GDPR: how to protect your data from the origin — you.
Internet Users Start Young
The average age of a child getting their first smartphone is 10.3 years old. Not to mention how much earlier they are exposed to and participating in online activities and associated apps. As the internet is arguably one of the most powerful tools that we can access why do we not then consider extensive tutelage, training, and preparation of the appropriate uses for this tool and how to protect oneself from those that exploit this tool in search for easily targeted victims?
Courses and training for children starting in kindergarten should not just be explored and considered but, without question, immediately implemented. So long as a child is in an educational (especially public) institution then they should be trained on the largest and most accessible public tool in humanity’s history. So in the United States that is a class from Kindergarten through Grade 12.
The internet will be an asset to any child as they learn how to find and use resources found therein to aid them in their growth and education. Here I make the point that it’s not a question of IF and WHY, but HOW and HOW SOON. There is the need for learning institutions to not only bring in experts to train and educate children and youth in assembly format, but also the need to implement full curriculum programs with trained and certified educators. Much as children and youth are required to attend physical education, sexual education, and drivers education courses they should also attend internet usage, basic coding, and cybersecurity courses in order to prepare them for life.

Software and Browser Extensions to Protect
Many websites and also cybercriminals rely on you not securing your settings or enabling software to block any non-consensual sharing of personal data.
Use a Firewall
Hardware and software firewalls are safety mechanisms that protect your valuable online information. They’re designed to safeguard users from security threats on the Internet. If you have a router, you should use at least one type of firewall. You don’t necessarily have to run both types of firewalls, but doing can only help. Although they overlap in some ways, they each have unique benefits that can help keep you safer online.
Generally speaking, there are two layers to a firewall. These work in conjunction with both hardware and software to carry out a predefined set of rules. This is a good thing, because online attacks are multifaceted. Just as there’s variability from fire to fire in real life, most online attacks differ in some way or another. To combat this, you need to have a comprehensive protection plan in place.
VPNs (Virtual Private Networks)
There are a variety of ways that we have covered in the past that allow you to secure your connection and transmitted data. Virtual Private Networks (VPNs) allow you to securely and confidently connect over the internet.
VPNs use two main methods to secure your data. First, the data is encrypted. This means it is converted to a secret and highly complex code with only the authorized recipient of the data holding the key to unlock the code and restore the original message. Next, the VPN wraps your data in a tunnel and extends the tunnel along the route to your destination.
In reality this tunnel is special software that is designed to detect attempts to compromise or spy on your data as it travels from point to point. Should any attempt at intrusion occur, the tunnel is automatically shut down and reopened using another route. Like knowing there’s a bad guy lurking on the street corner, so you don’t go that way, you choose an alternative and safer route.
Web Browser Extensions, Browser Security Settings for Internet Security
Using a web browser extension for internet security can lead to security breaches. Those in search of security are often scammed by those offering fake security. That being said, there are a number of legitimate browser extensions that aim to protect your privacy and connection. Some have been developed by nonprofits such as the EFF (Electronic Frontier Foundation) who specializes in protecting civil liberties in the digital sphere. The EFF developed https:// everywhere that automatically directs you to the encrypted version of a website if it exists and helps protect your communications and transactions on that website. Other legitimate security, which are ad blockers, tracking blockers, and more are extensions that have been developed for monetary purposes, which either you have to pay for or you consent to sharing browser data, such as Ghostery.
With some research you can build a browser that has functioning security extensions that do just as their name describes, they act as a tool and extension of your internet experience while helping enhance security. You can read in full detail our write-up on the best web browser extensions for internet security. We also have an article on the pros and cons of adblockers including how to customize your pop-up or ad blocker.
In addition to extensions you should adjust your privacy settings in your browser. Every browser is a bit different but here are good guides for Chrome, Firefox, and Edge.
Protect Yourself on Social Media
Social media platforms like Facebook and Twitter have privacy settings that you can adjust in order to have varying levels of visibility and security. It is important to learn how to adjust these settings and the impact of these adjustments. While adjusting your Facebook privacy settings is important it is also important to be aware of what you are clicking and reading.
Sometimes, clickbait leads to a website that’s riddled with adware, also known as Advertising Supported Software. If you accidentally install adware onto your computer, you’ll probably start to see unwanted banner advertisements. Adware’s main job is to collect information about you to show you catered advertisements. There is risk in clicking clickbait and especially filling out forms, surveys, etc. available on clickbait website. We saw the significance of that with the events surrounding Cambridge Analytica and the 2016 presidential election. Read our tutorial on how to discern clickbait and how to navigate it securely here.
Another danger on social media is the infamous “fake news”. While this may not be immediate danger to your data you are oftentimes targeted based on your personal data. Due to its severity and impact scholars are even in on the game on this one. GDPR can’t protect you from fake news, only critical thinking and an investigative approach cures this ailment and its extensively adverse consequences in society. For that reason we have a tutorial on key questions to ask when approaching “news”.
Conclusion
This is no denying that GDPR changes business and user processes at a fundamental level. It should have. But no major legislation or change should be enacted without critique and close observation. If not, we will be unable to make the necessary adjustments when the first pitfalls arise. GDPR more than likely will be an evolving piece of work that changes as new tactics arise that aim to circumvent what GDPR strives to protect, which is the user and their data. One would hope that governments are held to similar standards as businesses. An internet user’s fundamental rights does not cease to exist when the server and technical stack hosting the data is government owned… or does it?
While legislation is handy and protective it hardly stops the cleverness and motives of cybercriminals. More important that a safety net provided by legislation is an educated, critical, and capable internet user. This paradigm shift in legislation should also correlate with a paradigm shift in how upcoming generations are schooled in practice and theory concerning the tool that is the internet. There is no one that can protect yourself and your network better than you. GDPR does not prevent clickbait, misinformation, and social engineering. These are things that the user must learn to discern.
Many that have grown up with or heavily utilized the internet understand that the ethos of the tool is to breach geopolitical borders, to experience interconnectivity with humans in any place at any time. Governments have in recent years taken many measures to regulate and control this vital tool for humanity. In doing such we begin to see the geopolitical boundaries formed before the internet start to form while on the internet. Will this lead to divisions that we have worked so hard to overcome with the assistance of the internet? Going after technocrats or groups that exploit data is admirable. But are we squashing the ethos of the internet that benefit and unify humanity in the process? It’s a fine line being walked and one we’ll closely watch.