Table of Contents:
- What Is Two-Factor Authentication
- Why Two-Factor Authentication Matters
- How to Set Up and Use Two-Factor Authentication
Security matters now more than ever as the power of the internet has steadily grown, so too has the potential for its abuse. Whether it’s accessing bank accounts online or merely using a fun new app, your private information can be stored, and even shared, in all kinds of nefarious ways without you ever knowing.
While it would be nice and simple if old-school passwords could safely seal your valuable info away from prying eyes, even complex ones using letters, numbers, and symbols fall woefully short of providing real protection. Studies have shown cyber-crime is one the rise in our increasingly digital world, and while this cannot be outright stopped, the means do exist for individuals to defend themselves.
A solution many see as the future is one that is already partially in use, and has proven itself incredibly effective precisely because it is relatively simple. Two-Factor Authentication, commonly referred to as 2FA for short, just might be what the digital doctor ordered to keep data safe while also keeping your information and applications easily accessible.
Let’s run through what 2FA precisely is, why this kind of increased security matters now more than ever, and how to get started today setting it up on your devices and applications.
What Is Two-Factor Authentication
Two-factor authentication is a security system that involves an extra, and often personalized, step a user must take before being able to access certain information. In doing so, 2FA prevents your data from be used or spilling all over the internet if someone were to find or figure out your basic initial password.
An in-person example of this would be a cashier asking for a photo id when making a purchase by credit card or a pin number at an ATM. This prevents thieves who have stolen a card from being able to rack up a giant bill on someone else’s tab. With the extra step, the damage done by theft is minimized or outright avoided.
Online the same logic applies. A system which utilizes 2FA asks for secondary information beyond a normal password. The second step could be a time-sensitive text to your phone with a unique string of numbers, as only the rightful owner with the correct phone would be able to complete the additional step, or an email sent to a specific account for additional confirmation of identity.
There are multiple forms of 2FA, but the most common are email or an SMS — also known more commonly as a text message. There do exists physical forms of a 2FA such as a small USB friendly devices, applications developed solely for 2FA usage, but they all operate under the same basic principle of creating a second step.
Whatever format you decide use, all forms of 2FA achieve the same aim of keeping you safe and hackers at a safe distance from your sensitive information. Why this matter is a valid question, but also one which can easily answered by looking at the reality of the digital landscape.
Why Two-Factor Authentication Matters
A basic password is like having one wall between your data and attackers. It is a solid start, but it can’t be expected to hold up against all the external aggressive elements indefinitely. While changing your password periodically provides a fresh coat of paint for your wall, it doesn’t fix the core issue of it still being a relatively simple form of security.
Once the barrier cracked, it’s easy to pry open for further abuse like outright identity theft. The negative financial impact of this is immediate, but the time and effort it takes to undo could haunt you for months or even years.
By having two steps however, you give yourself not only another wall, but one which is a good deal more effective by virtue of having an interactive element.
This buys you time. If a threat is repeatedly entering the correct initial password but stumbles on the second step, most systems will alert you after a few failed attempts and lock the account. This is absolutely vital as it gives you the window of opportunity to further clamp down with your defenses before the aggressors actually get to your information.
While making your log-in process a little longer might seem unnecessarily arduous at face value, the safety of mind and data in the long term more than balance the extra minute or so it might require.
Once you get the hang of using 2FA it requires little in terms of extra time, and the breadth of security it provides is well worth the extra time required to set up and use.
How to Set Up and Use Two-Factor Authentication
Now that we understand what Two-Factor Authentication is and why it’s important, we can move on to actually setting it up on our computers and devices.
To get started with your own 2FA security system, you first need to decide what format you intend to use. In this guide we will cover SMS (text) and email formats as they are the most common and universal in style, and what we recommend starting off to get the hang of the process.
For most platforms like social, banking formation, or personal emails you will need to log into your account and look at your security settings. Usually their 2FA system is referred to as log-in verification, approval, or as 2-step verification seen in the example here.
See below for what this looks like with Paypal, a popular application used to transfer money via the internet.
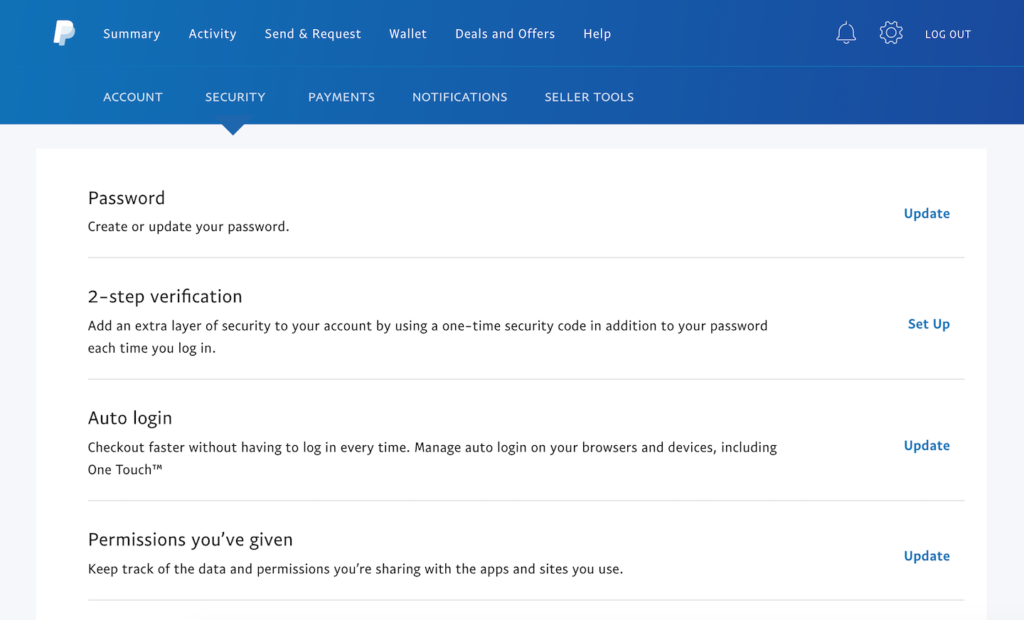
Here we can see a series of options Paypal provides for their users’ security. In the middle of screen we can see “2-step verification”, and to the right side the words “Set Up” highlighted in blue. This is what we want to click, and in doing so it leads to the next image.
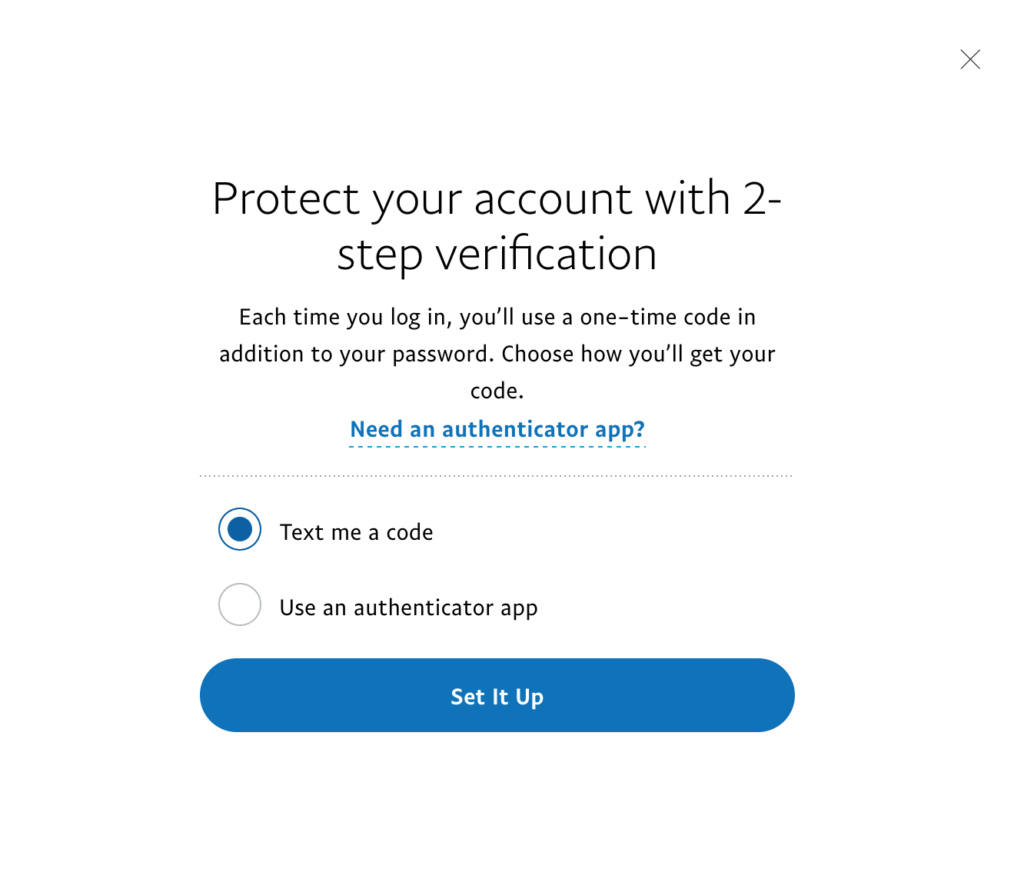
We have now initiated the 2FA set-up process, and the first step is to use a One Time Code (OTP for short) to verify it is working. With the “Text me a code” circle selected as pictured here, we can then click the “Set It Up” blue rectangle below to move forward. This will move us to the following screen.
Alternatively, if you already have an authenticator application already handy, then select the lower option and use the unique code provided by it.
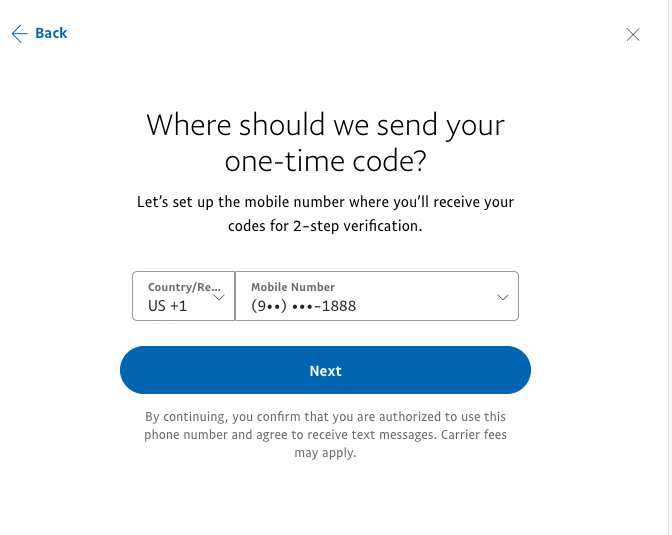
You should receive a text that looks like the image below, your unique OTP password of six-digits.
Note that within the text the time limit for when you can use this password is mentioned, and these are usually quite short. This is an additional level of security to ensure both steps are done within the same time frame, and that the password within the second step is not static long-term like a primary password.
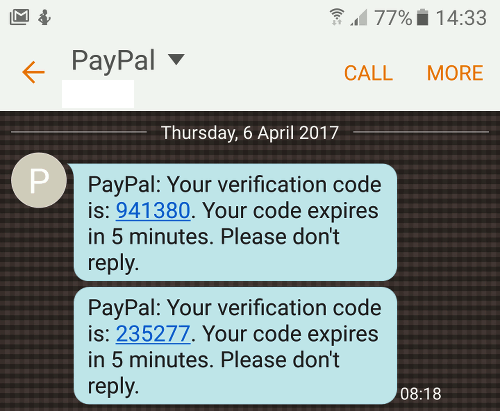
Write down or save the OTP from the text message, and return to the screen of the device we have been using thus far. It should now look like to the image below.
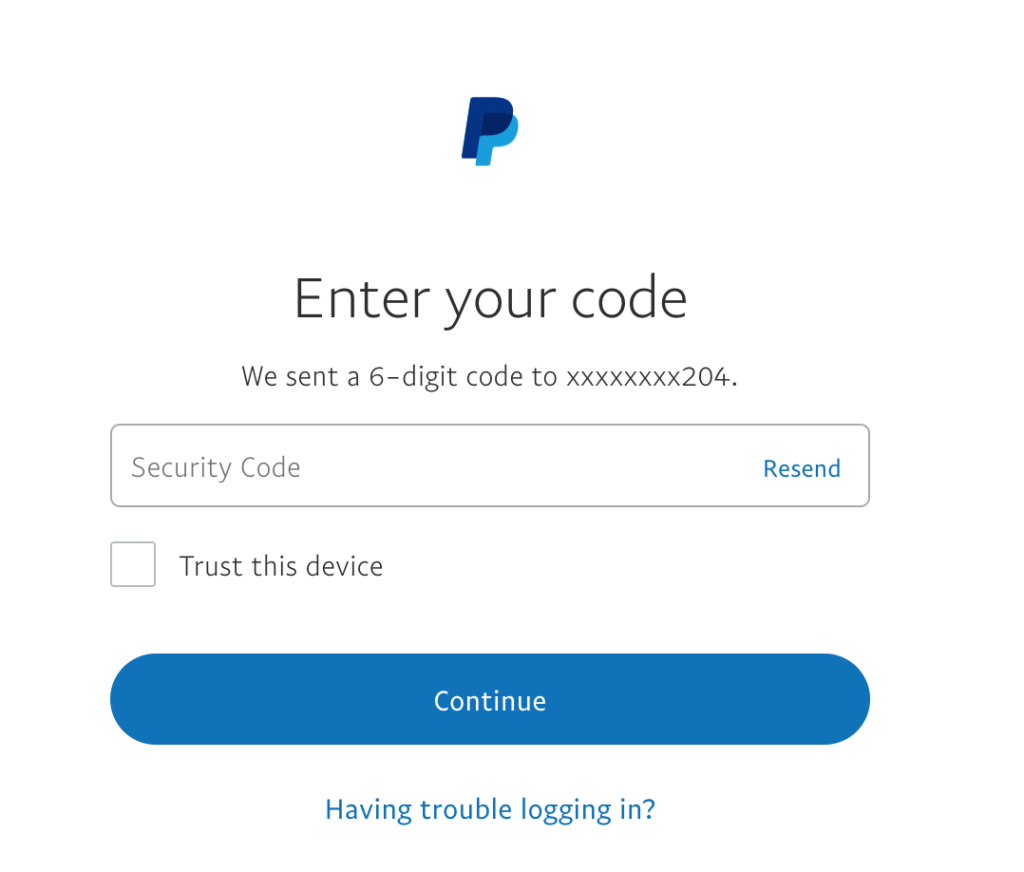
Enter the 6-digit code in the middle rectangle which reads “Authentication Code” in gray. Upon completion click “Confirm” in the middle rectangle below, and you are now safely set up with your very own 2FA security system!
When accessing accounts with 2FA security enabled, you will be required to perform these actions again. Make sure your associated phone number or email with you account is up to date so it all runs smoothly. It’s the same process every time, the only variable being the numbers that compose the OTP password sent.
If for some reason you enter the wrong code, or fail to do so within the time limit, that’s ok. You will be stopped from accessing your information, and the following screen will appear.
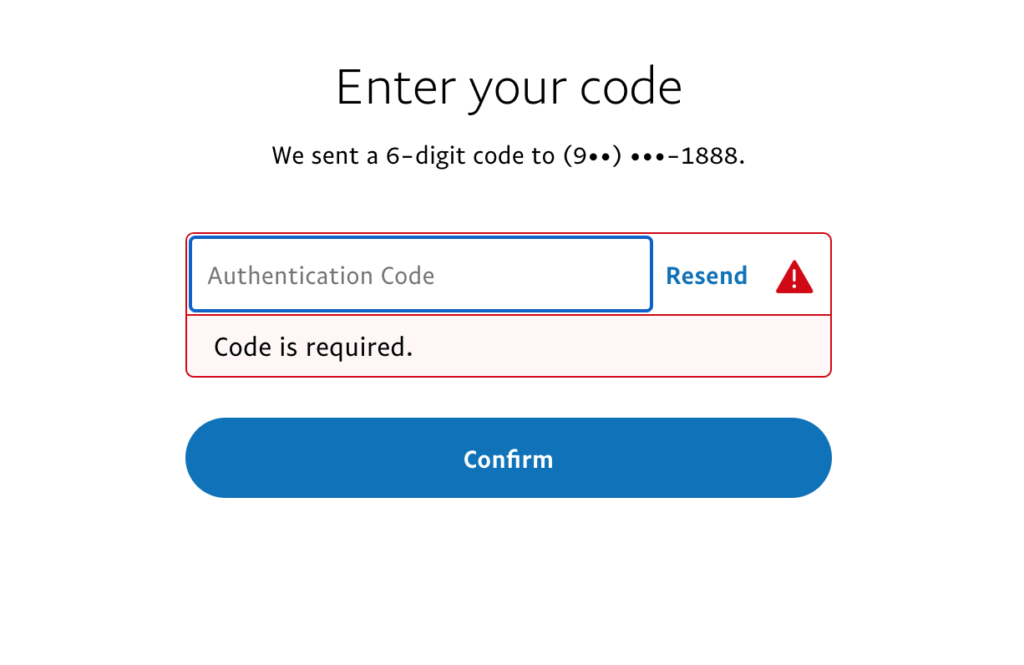
Simply click “Resend”, shown here to the right of the red triangle with an exclamation point, and try again. Be sure to take your time and be accurate on the follow up though, as too many failed attempts will result in a temporary lock of your account for most applications.
Once you successfully enable Two-Factor Authentication across your accounts and devices, you are all set and a good deal more secure. The time and effort put forth will pay dividends down the line for your overall digital security, so kudos to you for being proactive!
If this seems a little overwhelming, that’s totally understandable, but don’t let that stop you from keeping your valuable information safe though, as we always have HelpCloud Technicians available for remote support to help resolve the issue. Drop us a line and we will happily advise you on how to best move forward with your Two-Factor Authentication set-up and overall digital security.
